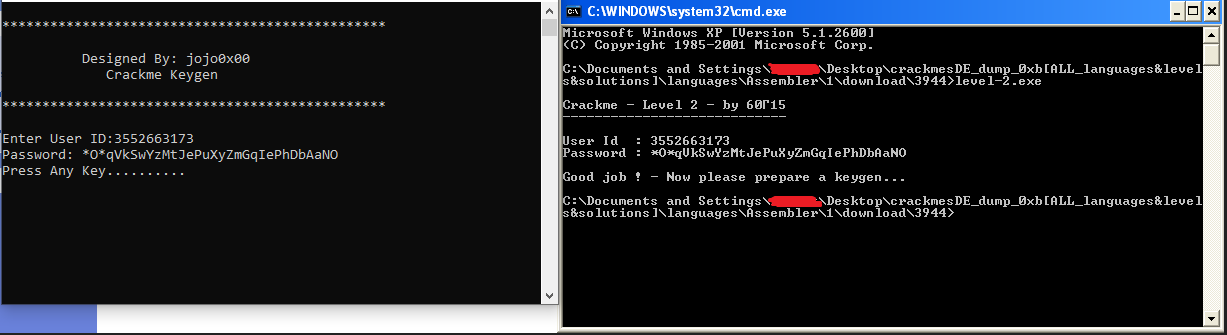
forn00bies Level-2
You can get Challenges here
Summary
- Getting the CPU Timestamp (Number of clock cycles from the last reset). See more here
- Making some tests on this Timestamp and modify this value.
- Generating the final password from these modifications.
Code Analysis
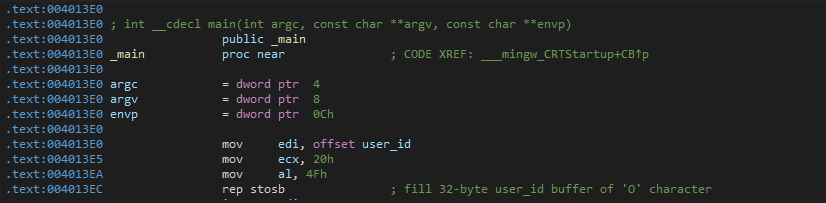
First, it initializes a buffer (user_id) and fills it of 32-byte of 0x4F (O character)
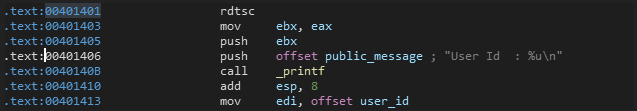
Then, it generates CPU Timestamp by RDTSC(Read Time-Stamp Counter) instruction at offset 00401401 and prints it out as User Id and moves this buffer into edi at offset 00401413. See more rdtsc
Now, there are some tests that the Time-Stamp Counter pass through first:
- Bit_Test.
- Comparison between Time-Stamp Counter and 0xB16B00B5.
- Parity Test.
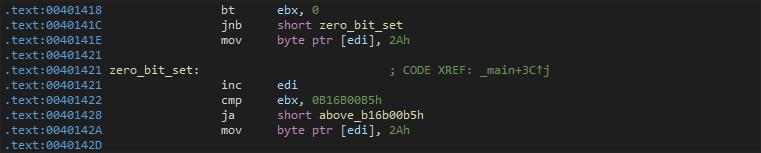
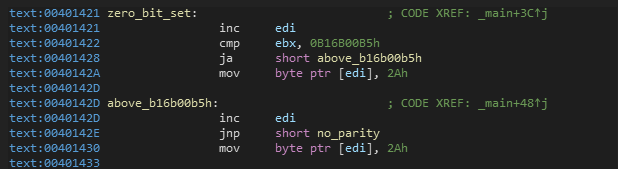
Bit_Test
It uses BT instruction to make a bit test at offset 00401418 and there is JNB (jump to zero_bit_set if CF == 0). See more bt
if not, it will replace the first byte of buffer with 0x2A (* symbol) and go to offset 00401421
if (Time-Stamp > 0xB16B00B5)
Now, it increases EDI offset to be 0040D021. Then, it makes a comparison between Time-Stamp and 0xB16B00B5 (jump to above_b16b00b5h if above)
if not, it will replace the second byte of buffer with 0x2A (* symbol) and go to offset 0040142D
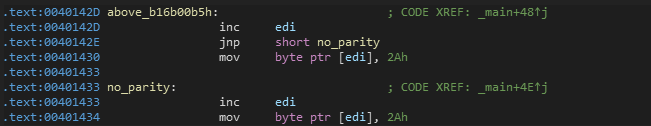
Parity Test
Last but not least, It increased the EDI by 1 and there is JNP (jump to no_parity if PE == 0). This jump will be never taken because PE is always set.
when EDI is increased, it will be 0040D022
(1000000 11010000 00100010 in binary) the least significant byte has an even number of 1’s so this jump is never taken.
Then it will replace the third byte of buffer with 0x2A (* symbol) and go to offset 00401433
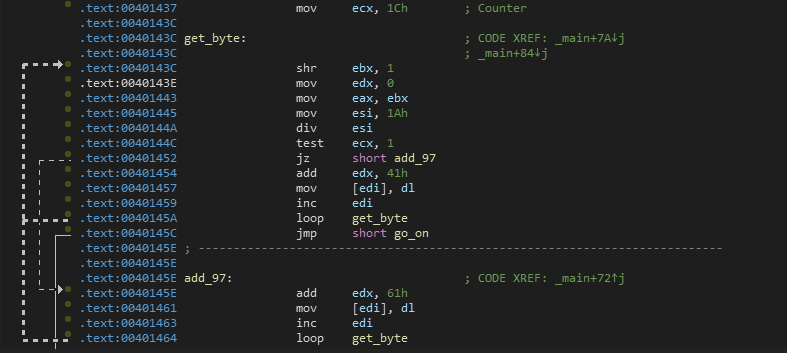
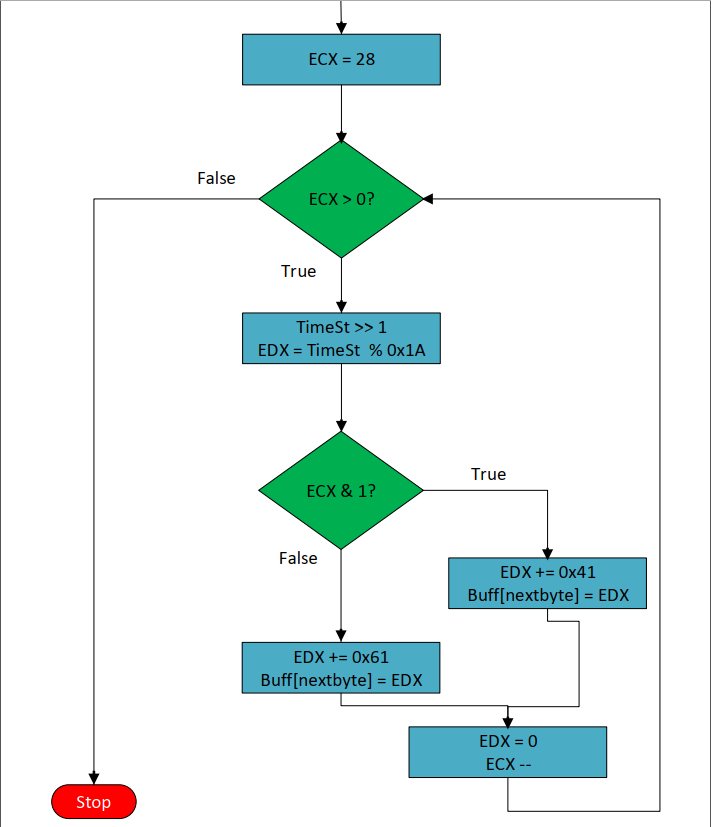
28-loop
Finally, it will make the last modifications to the buffer. It makes a loop 28 times, sets ECX as a counter, and initializes it with 0x1C (28). It makes the following:
- Shift-Right the Time-Stamp Counter by 1.
- Divide the result by 0x1A and put the remainder into
EDX. - Make a bitwise-AND operation with 1 and jump to offset
0040145Eif zero and add the next byte of buffer with 0x61. - Else it will continue to offset
00401454and add the next byte of buffer with 0x41. - Finally, set
EDXto zero.
As shown in this flowchart: