PowerGrid Crisis
You can get this challenge here
Summary
- This challenge is based on the value of the
CFflag.- Reboot.
- Enter EMERGENCY MODE (simple XOR).
- Reboot.
Tricky Password
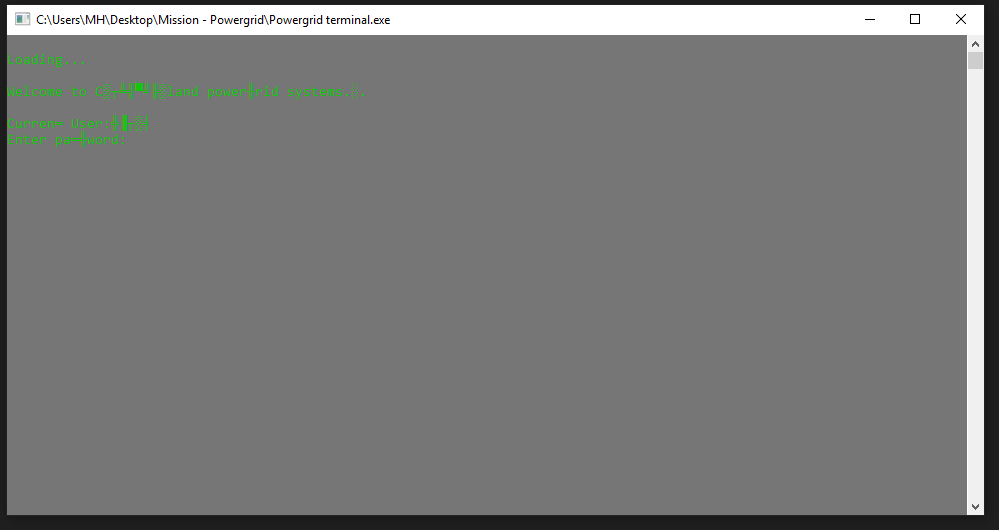
First, it asks for a password.
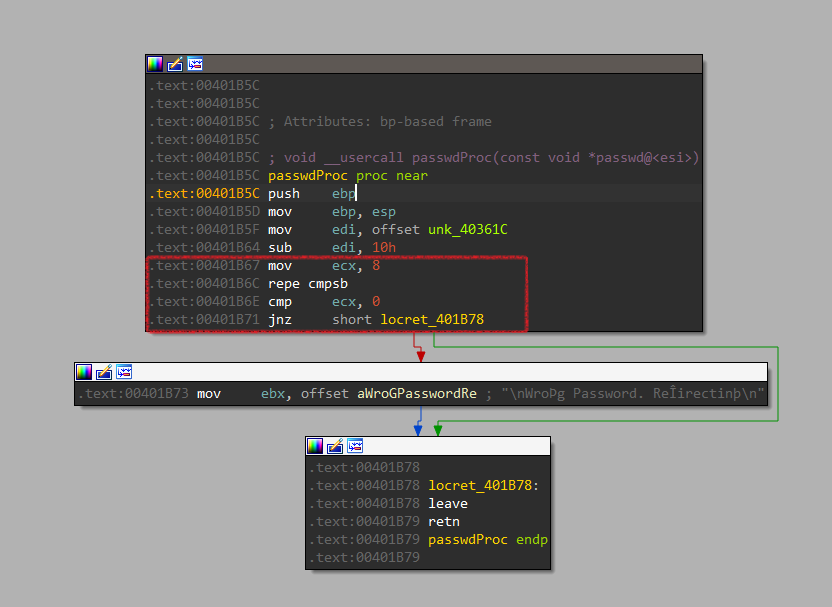
I tried to find it out but I realized it’s just a trick. It doesn’t matter because the password will be always wrong.
It compares the input with itself until ECX is equal to 0. Then it goes to (WRONG PASSWORD)
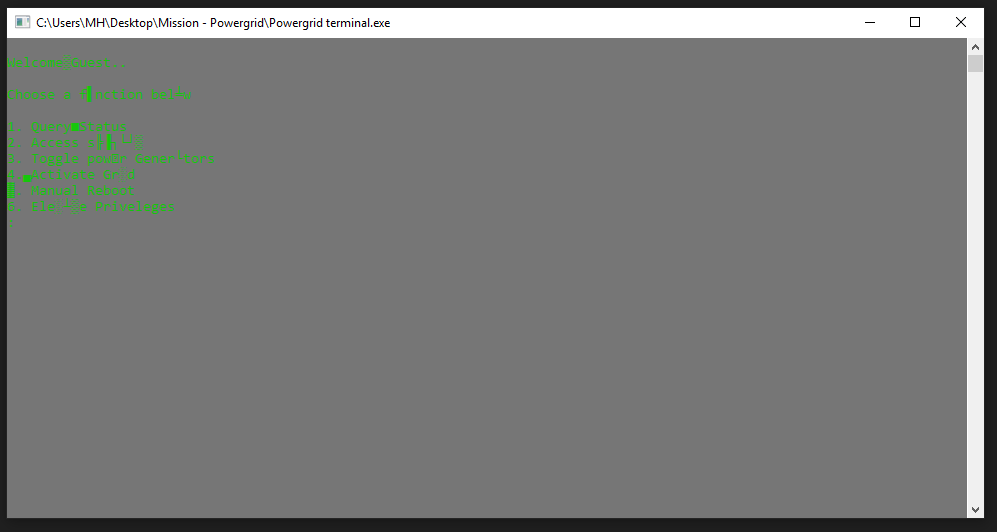
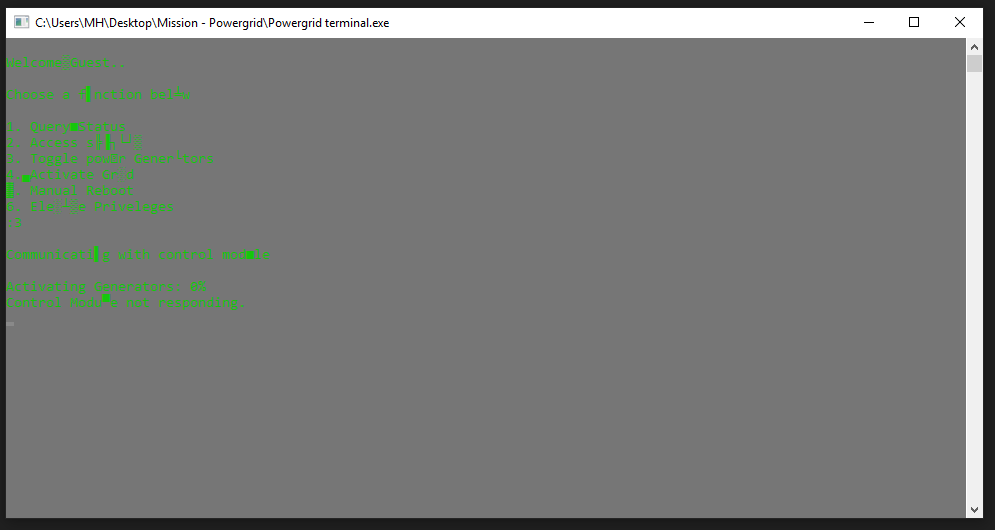
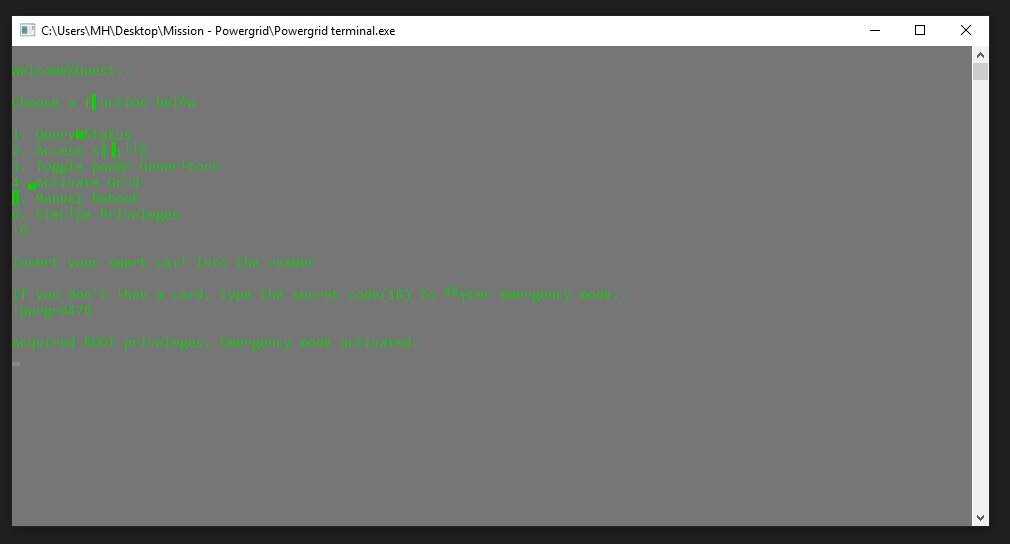
Welcome GUEST
Now, We have this window with these functions. It’s required to turn on the (POWER GENERATORS) to reactivate the POWERGRID so let’s try Toggle power Generators
Oops! It’s not responding. It’s time for Reversing.
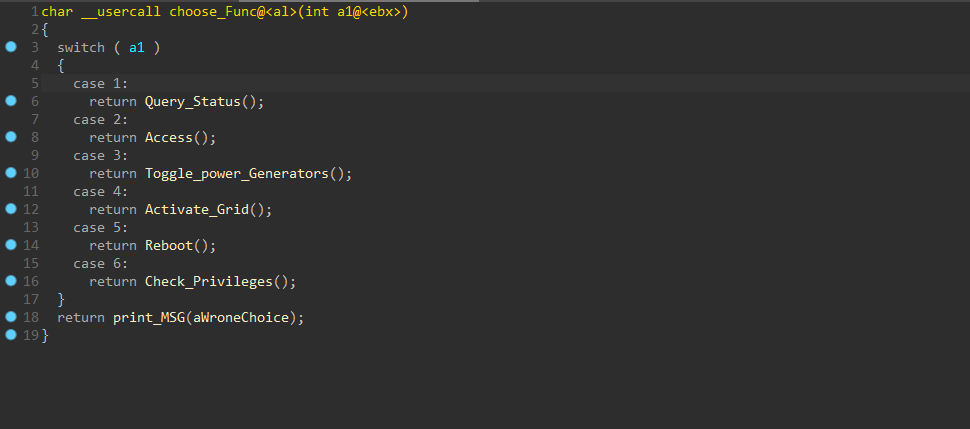
At 0x4016CF we have a function that contains a switch case. These are the available control modules of POWERGRID.
Let’s dig inside Toggle_power_Generators
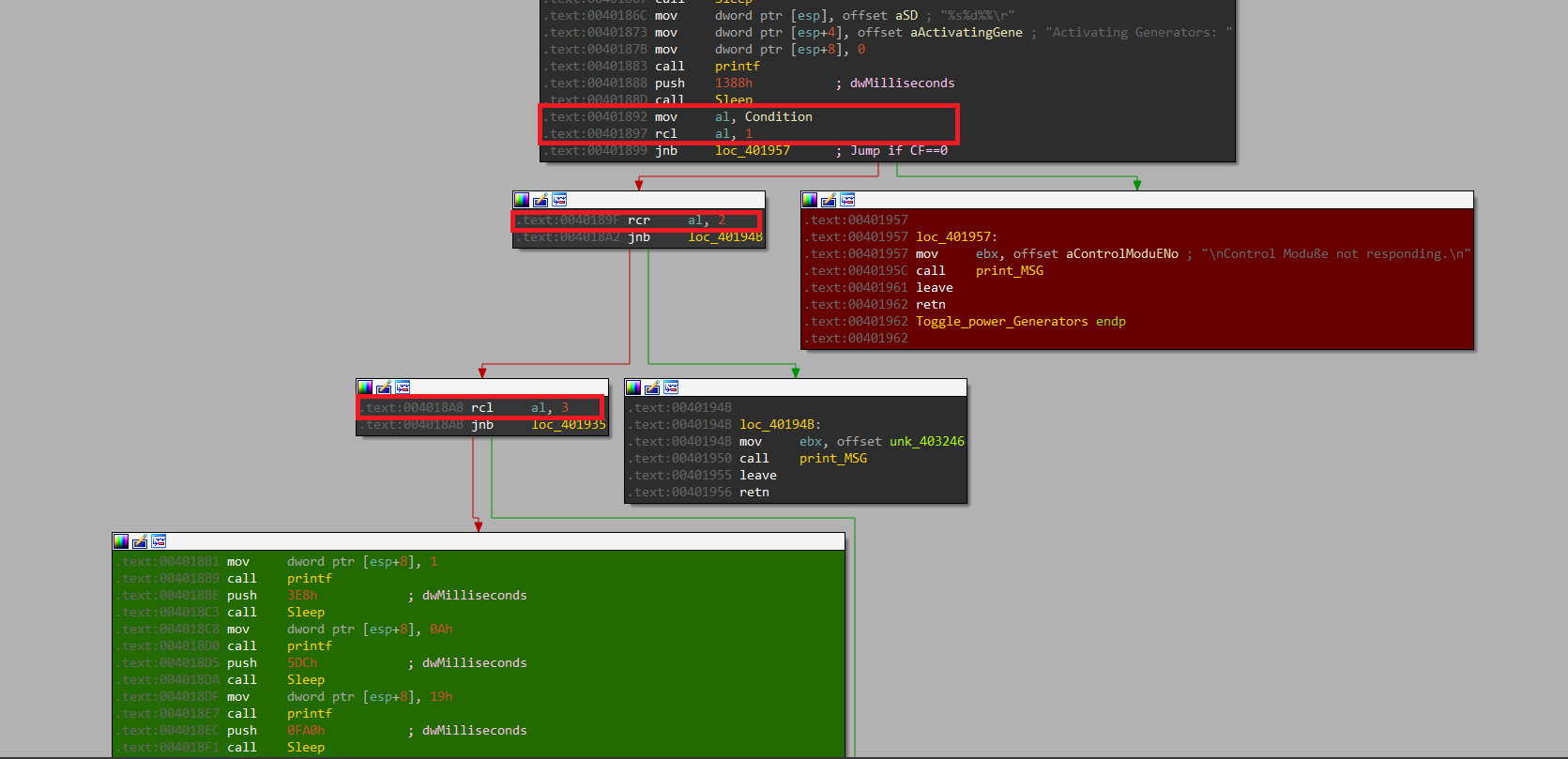
Toggle Power Generators
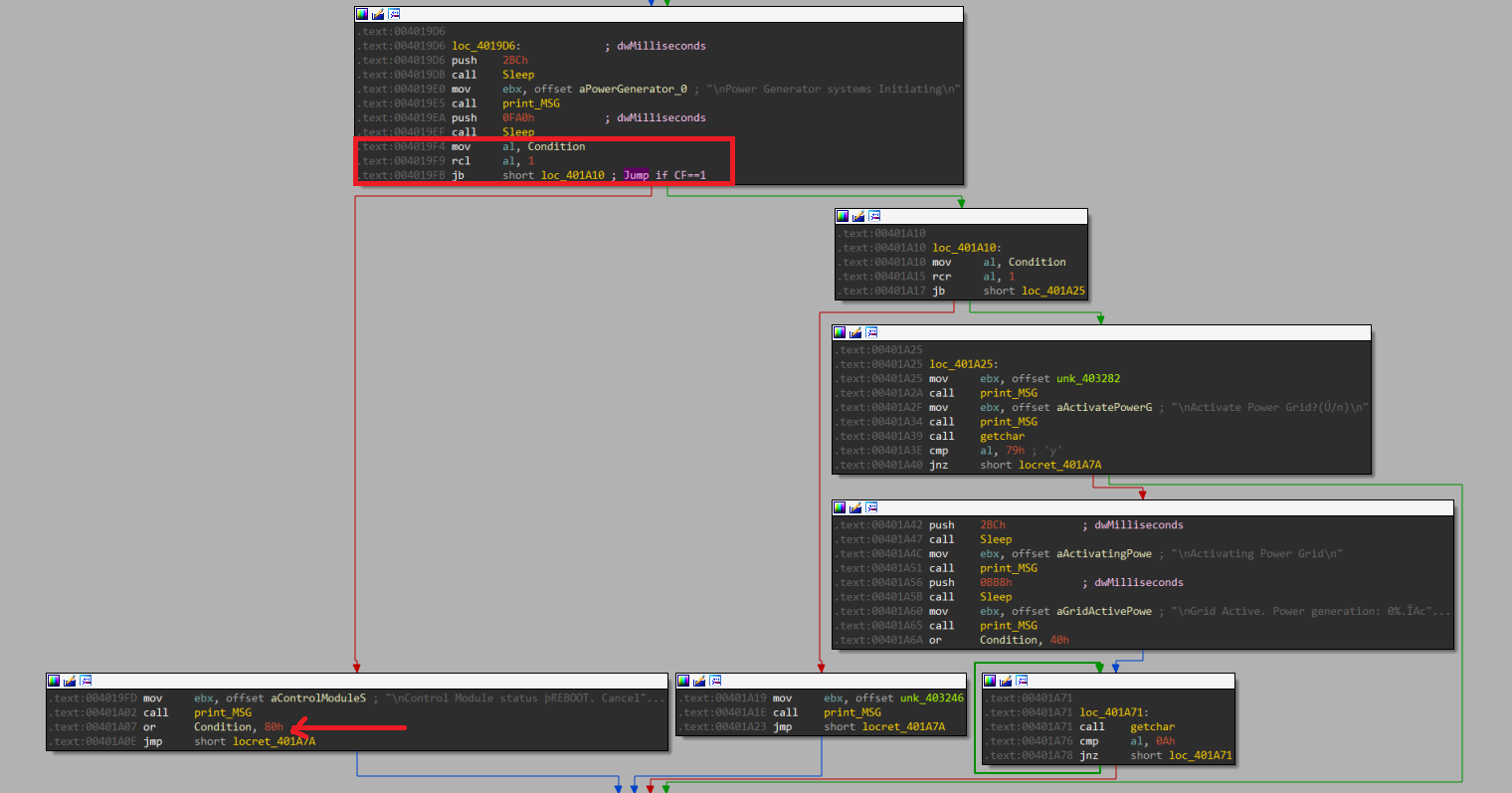
I don’t want the red area so I have to set the CF flag.
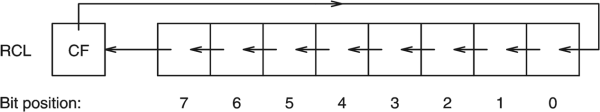
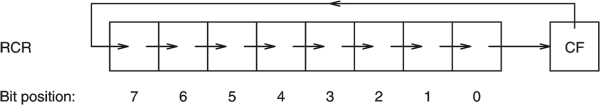
Here I see RCL and RCR, they are like SHR and SHL but they include the CF flag in the shifting
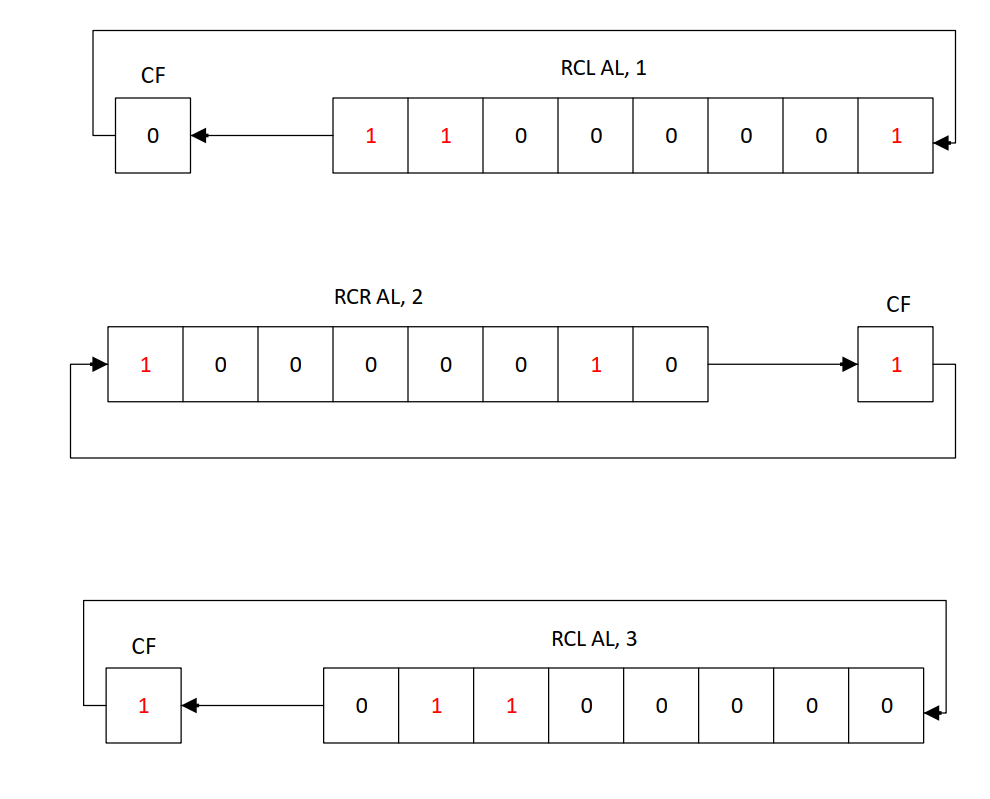
the condition variable is ZERO. This value is moved into AL and it makes RCL with 1 so I need to set suitable 1’s to set the CF flag and get into the green area.
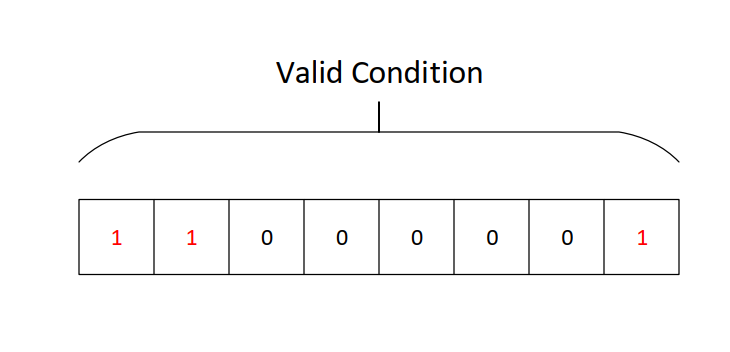
As shown, these are the valid 1’s that make the CF flag always set.
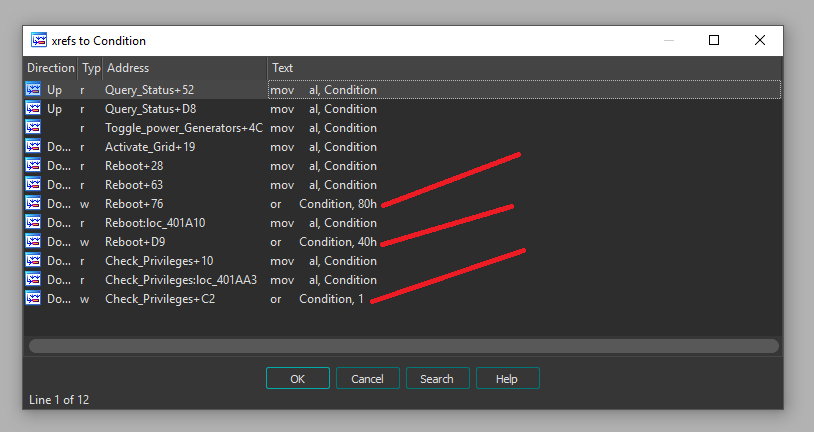
How to set these one(s)? This variable is OR-ed with 0x80, 0x40, 0x1 at these functions:
- Reboot
- Check_Privileges
So we need these operations to get the valid one(s) and turn on the POWER GENERATORS.
0x80 ==> 10000000
0x40 ==> 01000000
0x1 ==> 00000001
Final Sequence: 11000001
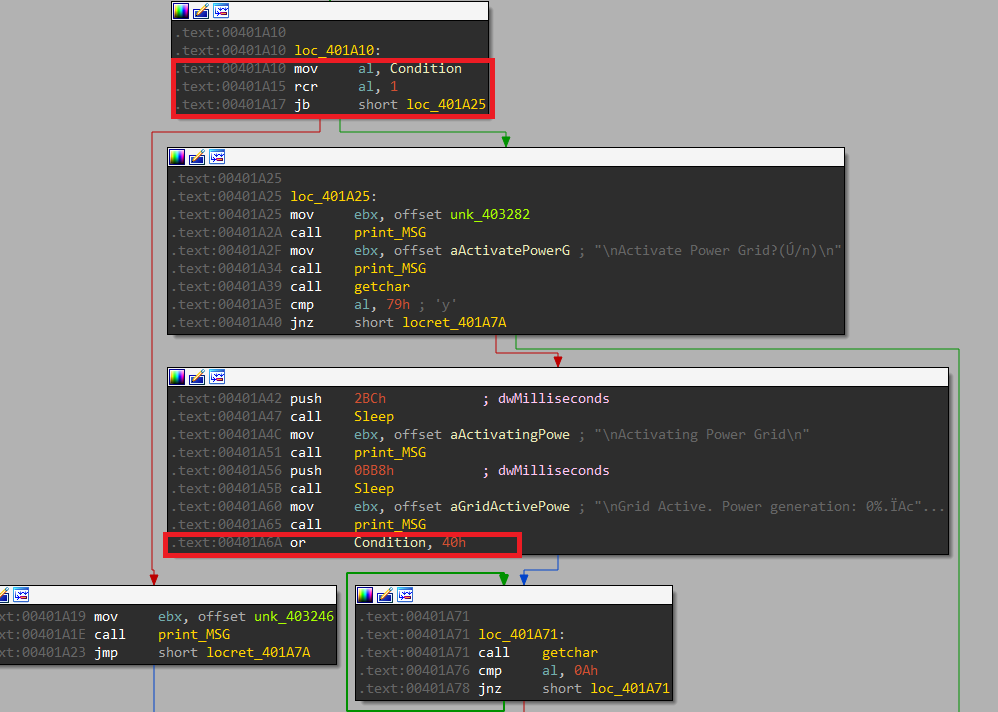
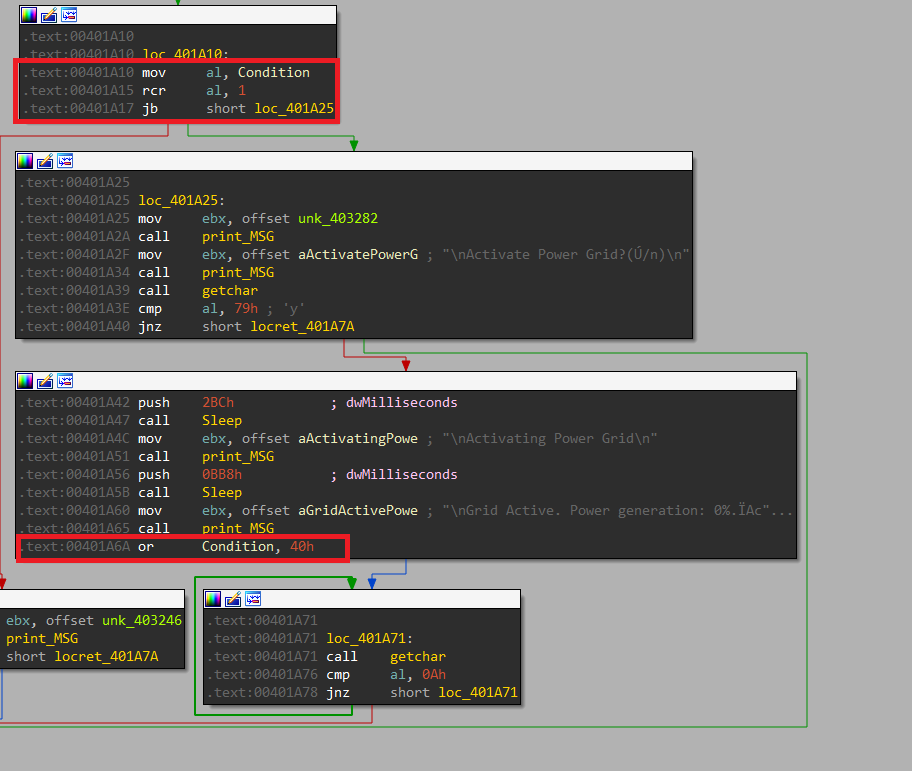
Reboot
Inside this function, there is an RCL operation with 1 but the condition variable still not set so the (CF == 0)
There is a JB (This jump is taken when CF == 1) but the false direction will be taken and the condition variable will be OR-ed with 0x80
I can see also another OR operation with 0x40 but there is RCR with 1 and the jump will not be taken because the first bit of the condition variable is not set.
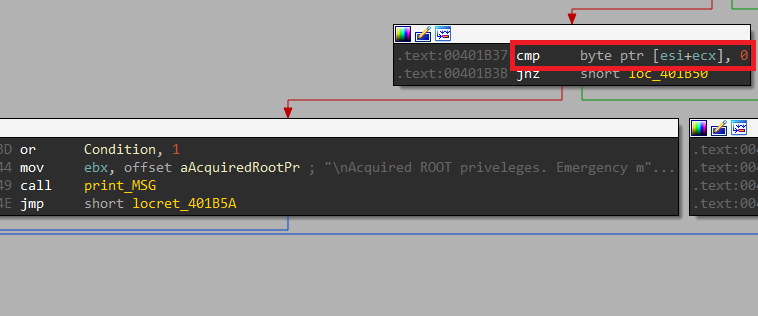
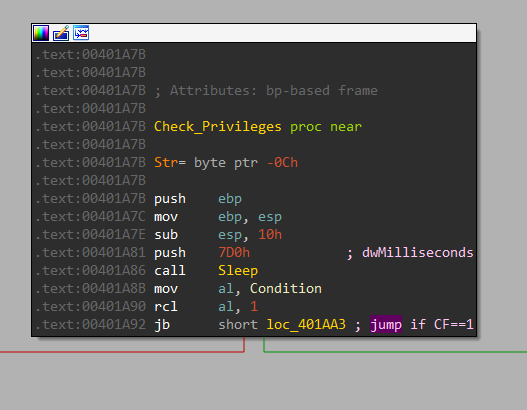
Check Privileges
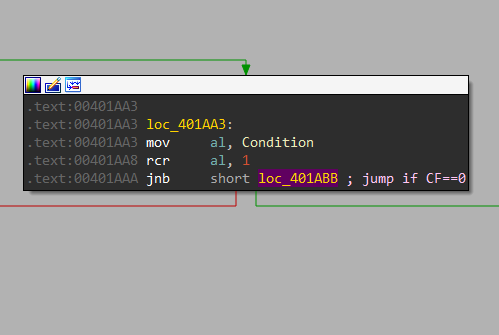
After getting the first one from the Reboot function, we can get into Check_Privileges for OR operation with 0x1.
Here, there is RCL with 1 and RCR with 1, the jump will be taken in both cases.
 |
 |
It asks for my smart card but I don’t have it. I only have to make some reversing to get the EMERGENCY SECRET CODE.
It’s very easy it’s just a basic XOR operation.
The idea of this operation is to make
ECXequal to zero; This will be useful to bypass this condition and get the OR operation
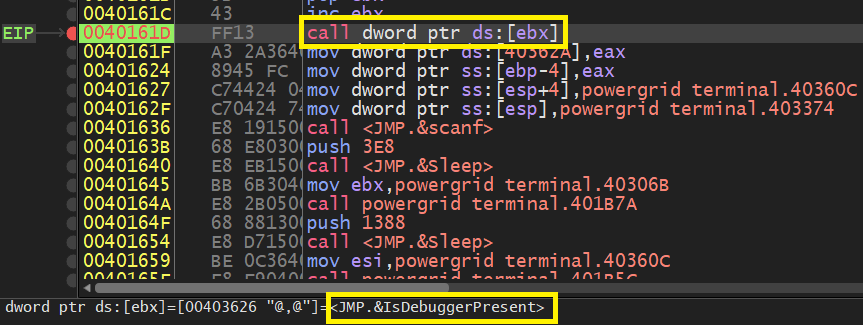
Before using our debugger, there is an Anti-Debugging Check we have to defeat.
At 0x40161D, there is a call to IsDebuggerPresent which checks the BeingDebugged Flag inside the PEB structure.
This flag is set if the debugger is used so we have to reset it to ZERO.
Let’s debugging now.
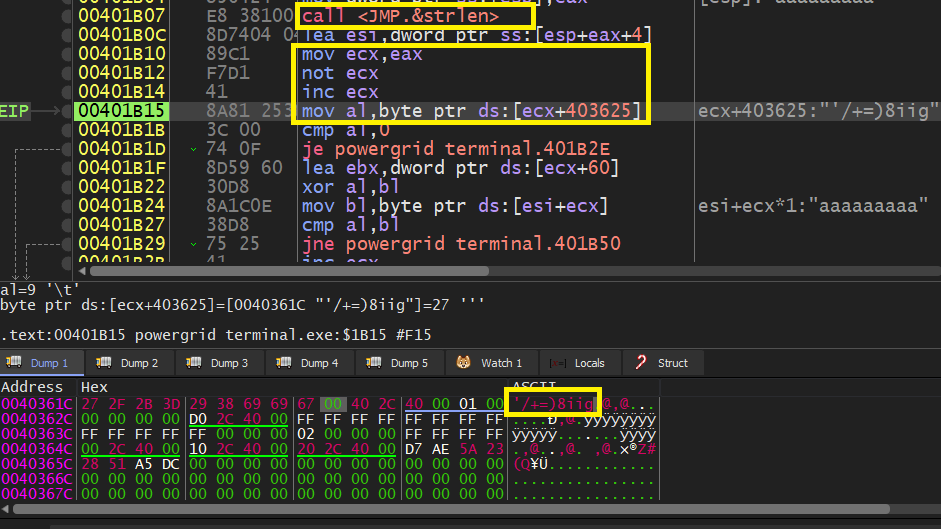
Here I see a wired string '/+=)8iig, in which each character is moved to AL based on the inverted value of CODE LENGTH.
To make it start from the beginning of this string, the code length should be 9.
Now, It XORs each character with a key starting from 0x57 to 0x5f.
With these pieces, I can generate the EMERGENCY SECRET CODE.
encryptedCode = "'/+=)8iig"
key = [0x57,0x58,0x59,0x5a,0x5b,0x5c,0x5d,0x5e,0x5f]
for index, keyElement in enumerate(key):
print(chr(keyElement ^ ord(encryptedCode[index])), end='')
output: pwrgrd478
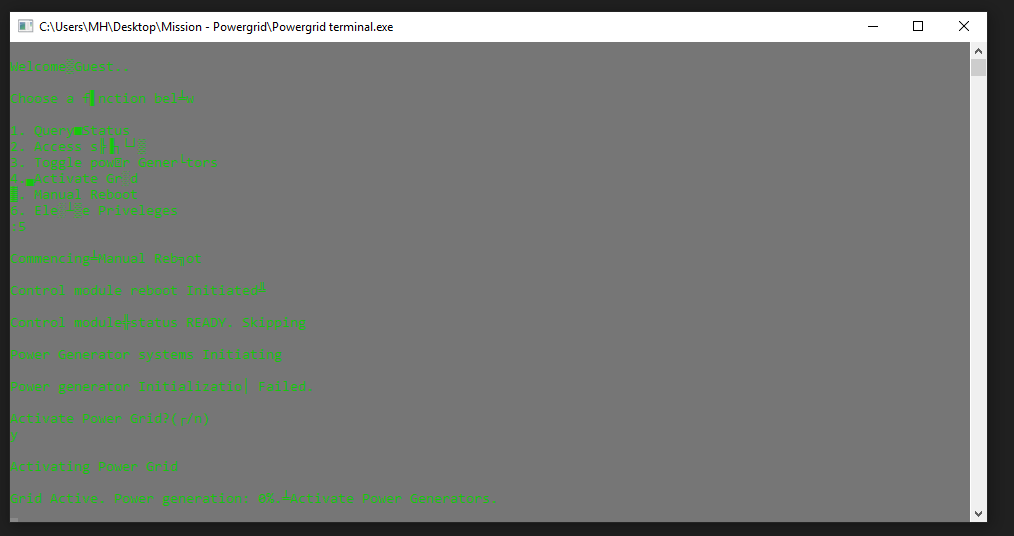
Now, Emergency Mode is Activated.
Reboot Again
The condition variable is 10000001, we can bypass the RCR operation and get the 3rd OR with 0x40
Crisis Solved
Generators are on. Power Grid is reactivated